Data Protection Software
Endpoint Data Protection Software
Data protection software exists because businesses understand the value of digital data, trying to protect this information on notebooks and desktops can be problematic.
To protect business data, it’s worth investing in a proven data protection software solution. We provide a world leading endpoint data protection software solution for your business.
Whilst disk technology has improved and SSD has prevented data loss due to robustness, the reliability of IT equipment is continually improving. Unfortunately, we’ve not yet reached the point where users seldom follow policy or know what to do, having endpoint protection certainly helps protect business data.
Below are some existing users.

What to look for in endpoint data protection software
Endpoint data protection software falls into one of two basic categories; file or block based. We are looking at protecting business data, not family photos. If you want to secure an endpoint device, it has to be a simple process to install and manage what could be 1,000’s of devices.
Alternatively, if you want to backup everything on an endpoint device regardless of content then you should be looking at backup software and not endpoint data protection. With GDPR they might want to know what your storing and how.
The endpoint data protection software we provide does not create an image, they are plenty of tools to do this and our aim is purely protecting business data.
Conversely, backup software is designed to backup everything on the endpoint device and copy the information to a local drive or cloud device. This as mentioned previously could be in breach of GDPR and might consume far more disk space that just protecting the business data.
How data is stored and where it is stored is also vital to a business wanting to know where files are stored and on what devices USB, HDD, network share, cloud application, SAN etc.
Choosing the right endpoint data protection software is a process of deciding what type of endpoint protection you are interested in having and then making sure that you have software that provides the right features and functionality a business requires.
What’s especially important is that the endpoint data protection happens when it is appropriate. That it doesn’t interfere with you using the system, and that in the event of a device being stolen you can protect business data.
Endpoint Data Protection software should be simple to use and enable you to license an unlimited number of endpoint devices. Business data should be protected using encryption and it shouldn’t affect the user.
Armed with this information you can choose the right endpoint data protection strategy for you, in order to protect business data from prying eyes.
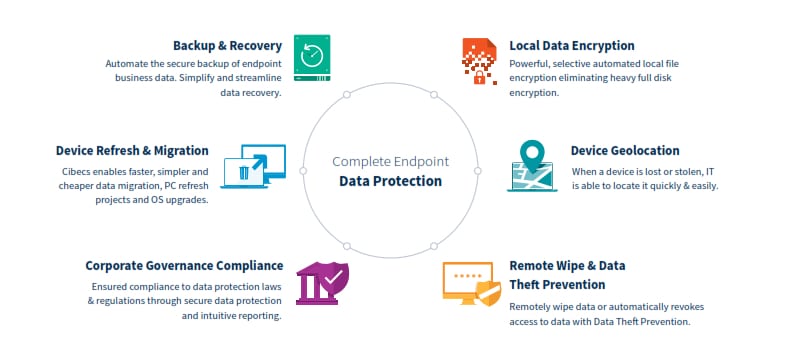
Endpoint Data Protection software is designed to protect Windows, Apple OSX devices and Linux. Cibecs offers complete data protection for your desktop and notebook computers by providing unrivalled protection across all devices to ensure you never lose data again.
Why Effective Endpoint Data Protection Software is Important
Many deployed notebooks typically have a shared drive where company data is accessed and stored. Once access to these areas is lost through network connectivity issues, users then store files on the desktop, my documents or other file locations.
As a result, large amounts of valuable and confidential business data remains unprotected and stored on user desktops and laptops with no way for IT to manage or protect it.
Unprotected Data is a Risk to Business
Whilst a business informs users where to store business data, seldom is this adhered to as users might have multiple documents open when connected to the internet and then the connection is lost. These documents then need to be stored somewhere.
Unrecoverable Lost Data
Files stored on laptops and desktops that are lost or corrupted often cannot be recovered. Causing wasted time, lost data and interruptions in productivity as well as financial and reputational damage.
Increased Infrastructure Costs
Storage & bandwidth becomes costly due to ineffective use of storage infrastructure, lack of data compression and data deduplication, and users storing personal data such as music and movies on the server.
Unprotected Business Data

Data on lost or stolen computers are vulnerable to unauthorized access. Sensitive business data is not effectively protected against data theft and security breaches.
Non-compliance to Corporate Governance Regulations
Companies are required by law to protect and archive their information as well as prevent unauthorized access to company information but have no way of effectively doing so.
Data Differentiation
Whilst businesses mandate that personal data on company property is prohibited, businesses are struggling to differentiate between a corporate video or home video and as such everything is backed up regardless of file type.
Secure Endpoint Data Protection Software for Business
With ever increasing disk capacities with desktops and notebooks out numbering servers by at least 100:1, the amount of business data residing on endpoint devices is huge and so is the possibility of data loss. How these devices are backed up causes continuous headaches for the IT department. Cibecs Endpoint Data Protection Software provides multiple ways and methods of securing business critical data.
- Backup to the Cibecs Cloud
- Backup locally to designated data storage systems
- Backup to your Microsoft Azure Tenancy
- Backup locally and then replicate to the cloud
Secure Data Encryption
All business data deemed important to a business is encrypted using policies and AES 256bit encryption. Encrypt business only data and exclude everything else. Data is encrypted on the Endpoint device and during backups.

Stolen Notebook
Revoke access to business data if the notebook is stolen. Geo location provides the functionality to locate your Endpoint device. Remotely delete files to prevent data theft.
When a device is lost or stolen, IT is able to locate it quickly & easily. IT can track the location of any protected device for quick recovery or remote wipe, increasing the chances of recovering your device and the confidential data on it.
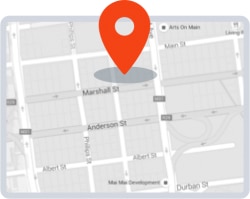
- Google Maps interface provides details such as street city, and country
- Displays the last-known IP address of every device
- Cibecs geo-location tracking is accurate within 10-20 meters
Protect All Your Cloud Application
Securely backup Office 365 documents including OneDrive, Email PST’s, Dropbox and Google Drive.
Single Instance Support
Ensures only a single copy of the data is copied throughout the enterprise greatly reducing disk space and network bandwidth.
Data Deduplication
Utilising data de-duplication and compression greatly reduces the amount of data stored and backs up block-level changes of files, drastically reducing the amount of available bandwidth required compared to a file backup solution. Cibecs globally de-duplicates any part of a file illuminating the need to store duplicate parts of any files by identifying and de-duplicates based on file type ensuring the highest reduction ratios. Data de-duplication occurs across all users at the object level ensuring that any duplicate data is only backed up once.

Centralised Management and Control
Managing 1,000’s of endpoint backup devices has historically been problematic due to the complexities involved in ensuring all devices are connected and protected.
In order to enforce the company’s data backup and protection policy, IT needs to have a complete oversight and central control over the end-user data backup and protection environment. It should be easy to configure, with the ability to import groups and users directly from Active Directory, with the added option of creating groups and users manually if required.
Deployment of data protection software should be integrated and simple to do. Central control should include the ability to centrally define data backup, encryption and other protection policies, central management of all backups, the ability to centrally customize the configuration and settings, and consolidated central reporting that enables IT to pinpoint potential data loss risks and act on these.
The backup agent should be simple to deploy and backup an endpoint device within minutes of the agent being installed. Perform a backup at certain times or opportunist backup 10 minutes after user login to ensure backup data is always up to date.

Granular, Intuitive Control over Backup and Protection Policies
Group users by department and apply specific department permissions to business data using a simple policy-based GUI.
Granular policy setting should allow IT to select both specific location and specific file types per department or user for backup. This means increased control over what data is backed up and elimination of wasted bandwidth and storage infrastructure.
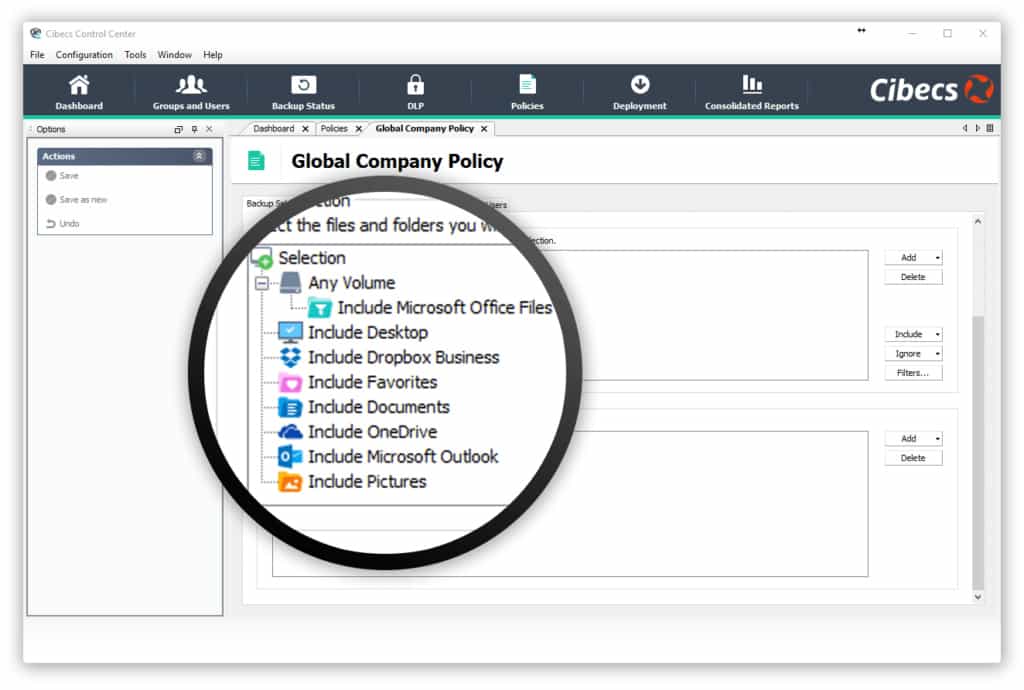
Departments will have different requirements for data protection software when it comes to selecting data for backups. For example, your Marketing team will need photographs and other media files to be backed up, where as your Finance department may not.
Granular policy selection with the ability to select data by file type also ensures that all relevant data will be protected as users often store their files in multiple locations on their machines.
This complete policy control given to an Administrator means increased data protection and less wasted infrastructure.
Fast and Easy Data Protection
An effective data backup and protection solution should allow for fast, wizard-driven data restores to ensure that data is easily recoverable when lost or corrupted. Data recovery should be a simple process reducing user downtime and IT resource requirements.
The data protection software solution must ensure that all user files are safeguarded from unauthorized access during the data recovery process, and that only an authorized IT Administrator or a user, with a specific key, can recover files.
The ability to quickly and easily recover and migrate user data to a new machine or operating system gives your business the added benefit of simplifying and accelerating data migration and hardware refresh projects. This will provide your organization with significant IT cost reductions as well as improved IT service delivery.
Centralised Reporting with Consolidated Metrics
Cibecs provides IT with simplified, real-time metrics for reporting on your data backups and data protection. You should be able to monitor your entire company’s data protection from a single consolidated metric, and narrow down to specific user groups and users to isolate any data loss risks and be able to address them.
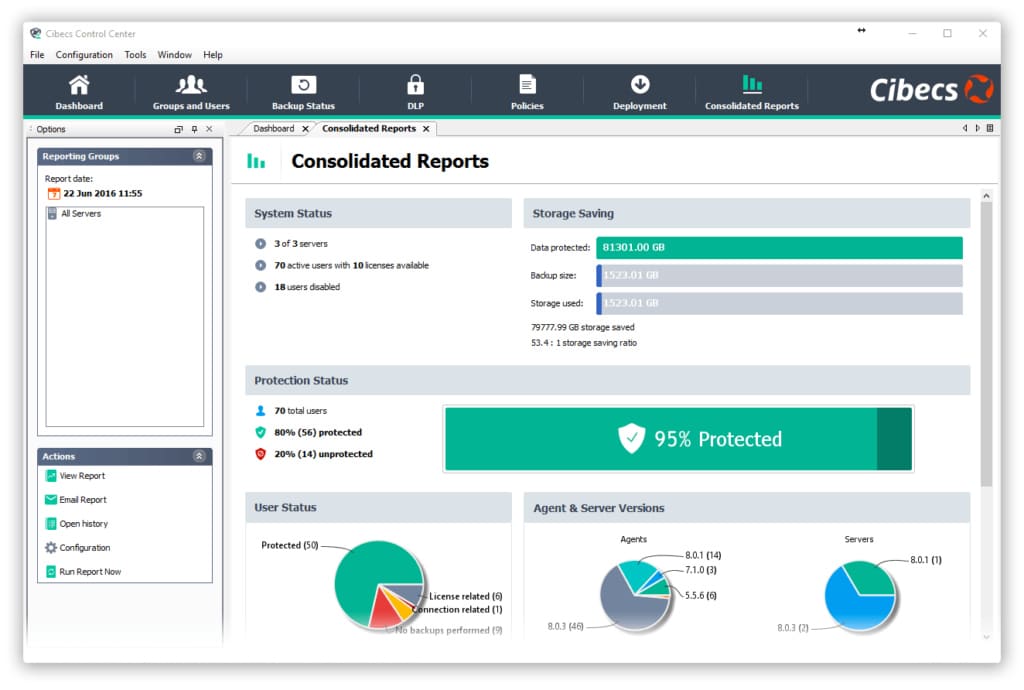
The management and reporting interface should be intuitive and easy to use, with powerful reporting and management features. You should be able to receive business and technical reports via email or in real-time, and track any data restores.
Ensure Corporate Governance
It has become a business imperative to protect sensitive company, customer and staff data from theft and unauthorized access, and for companies to be able to prove that they have a well-defined data protection strategy, that they have implemented this strategy and that they can monitor and report on it.

While the ability to backup and recovery data ensures that you are able to continue business uninterrupted, data loss prevention increase your data security and together ensure that your business is compliant with Data Protection legislation.
Full Inventory – Provides a list of all Endpoint devices in your organization
Asset List – Provides a complete list of all software/hardware including patches
Download the Endpoint Data Protection – 7 Must Haves